[This was thrown together at the last minute, so be aware that it is far from thorough. It's a real "cookbook" approach to getting going.]
For a Red Hat 7.2 system, install the following RPM's or later:
The gnupg RPM provides the actual encryption and signature software. Once you have it in place, run gpg once to establish a your ~/.gnupg directory and a default options file within it.
$ gpg --gen-key gpg (GnuPG) 1.0.6; Copyright (C) 2001 Free Software Foundation, Inc. This program comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under certain conditions. See the file COPYING for details. gpg: /home/kjcole/.gnupg: directory created gpg: /home/kjcole/.gnupg/options: new options file created gpg: you have to start GnuPG again, so it can read the new options file
I recommend editing the default options file and adding a keyserver by adding in one of the following lines:
keyserver search.keyserver.net keyserver wwwkeys.us.pgp.net
to the ~/.gnupg/options file. The keyservers search.keyserver.net and wwwkeys.us.pgp.net are searchable public key databases. They are actually part of a network of keyservers, that update each other, keeping all of them in sync.
Also, depending on your level of skill vs. your level of paranoia, you might want to add the line:
no-secmem-warning
which turns off the warning about GPG using insecure memory every time you use it.
Next, generate a keypair:
$ gpg --gen-key
gpg (GnuPG) 1.0.6; Copyright (C) 2001 Free Software Foundation, Inc.
This program comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions. See the file COPYING for details.
gpg: /home/kjcole/.gnupg/secring.gpg: keyring created
gpg: /home/kjcole/.gnupg/pubring.gpg: keyring created
Please select what kind of key you want:
(1) DSA and ElGamal (default)
(2) DSA (sign only)
(4) ElGamal (sign and encrypt)
Your selection? 1
DSA keypair will have 1024 bits.
About to generate a new ELG-E keypair.
minimum keysize is 768 bits
default keysize is 1024 bits
highest suggested keysize is 2048 bits
What keysize do you want? (1024)
Requested keysize is 1024 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 1
Key expires at Fri Sep 20 16:18:17 2002 EDT
Is this correct (y/n) n
Key is valid for? (0)
Key does not expire at all
Is this correct (y/n) y
You need a User-ID to identify your key; the software constructs the user id
from Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>"
Real name: Kevin Cole
Email address: kjcole@gri.gallaudet.edu
Comment: Gallaudet University
You selected this USER-ID:
"Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
Enter passphrase:
Repeat passphrase:
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
++++++++++.++++++++++.++++++++++.+++++.+++++++++++++++.+++++++++++++++.++++++++
++.++++++++++..+++++..+++++++++++++++++++++++++..++++++++++++++++++++..+++++
Not enough random bytes available. Please do some other work to give
the OS a chance to collect more entropy! (Need 171 more bytes)
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
.++++++++++++++++++++++++++++++++++++++++.++++++++++.+++++.+++++.++++++++++..++
++++++++.+++++++++++++++.+++++++++++++++++++++++++++++++++++>+++++.............
...............................................................................
..........................................+++++^^^
public and secret key created and signed.
$
REMEMBER YOUR PASSPHRASE! You'll need it to sign and/or encrypt your mail. You'll also need it to decrypt someone else's mail to you.
Now, you need to spread your public key around. First, you need to find out what it is. Assuming you're fairly new to this, your keyrings should be empty except for the single key you've just put in. So, type:
$ gpg --list-keys pub 1024D/E6F332C7 2002-09-19 Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu> sub 2048g/8B2232AD 2002-09-19
Jot down that 8-digit hex number E6F332C7. That's your Key ID. You'll need it later.
The pine RPM supplies the following shell scripts:
/usr/bin/pinegpg
/usr/bin/pinepgpgpg-install
and a bunch of symbolic links to them:
/usr/bin/gpg-check -> pinegpg /usr/bin/gpg-encrypt -> pinegpg /usr/bin/gpg-sign -> pinegpg /usr/bin/gpg-sign+encrypt -> pinegpg /usr/bin/pinegpg-install -> pinepgpgpg-install
The install script pinegpg-install inserts the following filter lines into your ~/.pinerc file.
# This variable takes a list of programs that message text is piped into # after MIME decoding, prior to display. display-filters="_LEADING(-----BEGIN PGP MESSAGE-----)_" /usr/bin/gpg-check, "_LEADING(-----BEGIN PGP SIGNED MESSAGE-----)_" /usr/bin/gpg-check # This defines a program that message text is piped into before MIME # encoding, prior to sending sending-filters=/usr/bin/gpg-sign, /usr/bin/gpg-encrypt _RECIPIENTS_, /usr/bin/gpg-sign+encrypt _RECIPIENTS_
The mutt RPM provides:
/usr/bin/pgpewrap
/usr/bin/pgpring
/usr/share/doc/mutt-1.2.5.1/PGP-Notes.txt
/usr/share/doc/mutt-1.2.5.1/gpg.rc
/usr/share/doc/mutt-1.2.5.1/pgp2.rc
/usr/share/doc/mutt-1.2.5.1/pgp5.rc
/usr/share/doc/mutt-1.2.5.1/pgp6.rc
Add the following line to your ~/.muttrc file:
source /usr/share/doc/mutt-1.2.5.1/gpg.rc
(or copy the gpg.rc file and modify to suit your needs, then "source" your personal copy.)
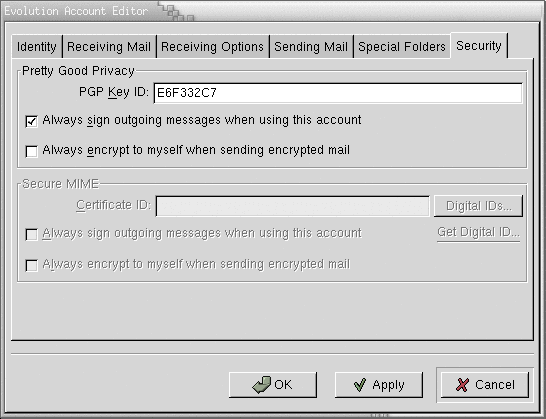
For evolution:





At this point, you should have three mail systems at least aware of how to sign/encrypt mail. You need to start spreading your key and collecting keys from other folks. First:
gpg --armor -o mypubkey.asc --export e6f332c7
That will create a file that one of my less computer-literate friends refers to as a "Borg". (If you're a Star Trek fan, it should be obvious why). It looks like:
-----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.0.6 (GNU/Linux) Comment: For info see http://www.gnupg.org mQGiBDy8MSURBACp4Iyqh88Fg6FG9Yc+Jrl+Qm5d5fDRJeYwPCdZHro5FP7XQDZX jqeJe08zZhKmOmCLNY59NQvt1Wa3RcAvdA7tqKIL7bbC6asZvK3DTm0RRVJs4Zq9 a6juBXhhjydZYISJuM9YstOkhh2oZzIotCKHxyBDwj4QObnboWH8EYo6GwCg7XXJ PlgOCsh4vF/9OwYQAipX6A8D/225NLmp4s9d3vIyZLgI/HZ24EcUMx1KZECzObfw hlSe31iJtOygs3YiQvM4TV3d08ELLJGSpJYPKa1WhcLiu+C9H2JYDR2fvwwYGojS 4t10ar7o1umBR1Kao18pCWT5Qq/mju22WwhtufYTiaWsod/OxRzsivGrMmX7Kv0v +kDwBACIwOaj2CHlFvMVUjaUE21/lgMNyzAqii6zGbA2oZctw3uAt2rXHtXtGkBg PCTQMLlYLf1QnIdnY/x89HhbqSrcbexgt9RNc6RK+WeBCQFmV6VnCAR2AGBZ8y8M +DX3sh3ZJJ1fnvDaEKyG23/yc9yTW2q2H4Bn+t5tw/l0i/W80rQ8S2V2aW4gQ29s ZSAoR2FsbGF1ZGV0IFVuaXZlcnNpdHkpIDxramNvbGVAZ3JpLmdhbGxhdWRldC5l ZHU+iFcEExECABcFAjy8MSUFCwcKAwQDFQMCAxYCAQIXgAAKCRCHzvTY5vMyx6he AJ9S1cs2qnxZ7Udc/4WpYOh9X1iYdACgrEbqdqUabFOhA6V26gnuLnJ2ZjuIRgQQ EQIABgUCPRMz3QAKCRDH7JTe5DHwzqm+AKCEFvnD2axp12oqbteDydourcRVmQCg m0a5jSS3jWOc+Xy4mg7VpfZzGrOIRgQQEQIABgUCPRNcyQAKCRBJ5FtX+inazjk6 AJwOE55QFgAwyNVk1ZB9gZaJFsnJmwCfZ5f/BmO46fcfhowqlKviK1sh8nGIRgQQ EQIABgUCPXTYyQAKCRDqMUWrLk6lLyolAJ9PTpkvZ0LixHIp0ecr2lCBYuQyiACf RFNK5pKv8JQBYhEEVBC4eAHdDiC5Ag0EPLwxOBAIAKH17kvzlFSvQcrFwwSkVCAq Dyy5urHYnxCT4HIJKQWWo3ffMK6aY4riVAdZS6eq0OoGadOOOO/tz1Akij+4BJvQ 1l9GKBN8MywlLFhB+1oE8PQfDyVrb029wFNLhFlSnJfzZZeAe+Tiu4GxLhccTmcC +vWkqNwiDDnIb5fuWP06iW0uZTztAXmWWTDPT0NeymjIve+xnEqq2qVRxGoiee+k CW5CwgNk/5bdzKp0eU3bFmTgwCEWQUCEUpAGe87uqvKJmLzFReva8Sosoc6DsNk/ VaVBO6NYSgjCt6oH26nchaMf2GP8Mx77uaEfc69+mDkIUAafc88OWQXnFt9TaysA AwUIAJkQy1uU5JpuQuPHRILOLPeQ+ZUhUnLDhC+A1d2j8nvK49Nu0NauDUdCEsVW LpN4c4t4+GukiB9nsEuPGg9klJ8BLaWhA6M1oH7a3ZR9eSjVzfBefnYEKSOSOt8d uradXzJ6EMuX4/XnXJZHJGfV6fP9ZKJs8iUt8r+E3YTuQVBxQzCaB+OI08V40veM w2xHkE2ntp0OREo0cOFlZqRlnkp6/3/CqrDRdmAtFIR8mmW0VqQgAiOr1hkUpeXt f2P2MvyJOloBN6+PEzqZk4rBGsW3OcNaTK4BLsV7xDsxfcQYguR3mPEF54CRY5ad JbSHuAOH9tANnhXwGBmbF4YgscGIRgQYEQIABgUCPLwxOAAKCRCHzvTY5vMyx/7z AKDI6+U7+a4dcbGsG4uztXSA/uDNOQCgnkP+uhxWhIpCqgMD8yMyWHLPsFo= =yaOl -----END PGP PUBLIC KEY BLOCK-----
This is the file that you'll want to ship around to keyservers, send to people via e-mail, and put on some web page somewhere. It's also nice to include your Key ID on your regular signature files. Or, you can insert the longer "fingerprint". To obtain your fingerprint, type:
$ gpg --fingerprint e6f332c7
pub 1024D/E6F332C7 2002-09-19 Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu>
Key fingerprint = 75E2 0A77 FC0C 2128 F3B3 AA07 87CE F4D8 E6F3 32C7
sub 2048g/8B2232AD 2002-09-19
You can go out to a keyserver, and get someone else's public key, usually by either searching on their e-mail address, or their Key ID. (Note, some servers want you to specify "0x" in front of the Key ID, so that they know it's a hex number you're feeding it, and not an e-mail address. Once you have someone's key, cut and paste it into a text file, then add it to your keyring with:
gpg --import theirpubkey.asc gpg: key E431F0CE: public key imported gpg: Total number processed: 1 gpg: imported: 1
Later, if you have a chance to meet the individual who has sent you a key, and they can prove who they are by both showing you a government ID, and producing their fingerprint, you can sign their key, thus lending more credibility to it. (See "Web of trust" elsewhere.) To sign a key, first get their key ID from your keyring. Then you can either sign it from the command line or "edit" it and sign it from within the edit environment. Like so:
$ gpg --list-keys | grep -i fede
pub 1024D/E431F0CE 2002-01-16 Federico Grau (personal key) <donfede@casagrau.org>
pub 1024D/2E4EA52F 2002-08-20 Federico Grau (work key) <grauf@rfa.org>
$ gpg --sign-key e431f0ce
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: -/q
sub 2048g/ADF8AF54 created: 2002-01-16 expires: 2005-01-15
(1). Federico Grau (personal key) <donfede@casagrau.org>
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: -/q
Fingerprint: 0DA1 7607 5FCA E3E4 18B4 EF73 C7EC 94DE E431 F0CE
Federico Grau (personal key) <donfede@casagrau.org>
Are you really sure that you want to sign this key
with your key: "Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu>"
Really sign? y
You need a passphrase to unlock the secret key for
user: "Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu>"
1024-bit DSA key, ID E6F332C7, created 2002-04-16
Enter passphrase:
The other way to do this is with the "edit" option, which gives you the ability to set the "trust" of a key among other things:
$ gpg --edit-key e431f0ce
gpg (GnuPG) 1.0.6; Copyright (C) 2001 Free Software Foundation, Inc.
This program comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions. See the file COPYING for details.
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: -/q
sub 2048g/ADF8AF54 created: 2002-01-16 expires: 2005-01-15
(1). Federico Grau (personal key) <donfede@casagrau.org>
Command> sign
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: -/q
Fingerprint: 0DA1 7607 5FCA E3E4 18B4 EF73 C7EC 94DE E431 F0CE
Federico Grau (personal key) <donfede@casagrau.org>
Are you really sure that you want to sign this key
with your key: "Kevin Cole (Gallaudet University) <kjcole@gri.gallaudet.edu>"
Really sign? y
Command> trust
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: -/q
sub 2048g/ADF8AF54 created: 2002-01-16 expires: 2005-01-15
(1). Federico Grau (personal key) <donfede@casagrau.org>
Please decide how far you trust this user to correctly
verify other users' keys (by looking at passports,
checking fingerprints from different sources...)?
1 = Don't know
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
s = please show me more information
m = back to the main menu
Your decision? 4
pub 1024D/E431F0CE created: 2002-01-16 expires: 2005-01-15 trust: f/q
sub 2048g/ADF8AF54 created: 2002-01-16 expires: 2005-01-15
(1). Federico Grau (personal key) <donfede@casagrau.org>
Command> quit
Now you can take the signed and trusted key, export it again and send it back to the original owner. You can also post it to a public keyserver.
gpg --armor -o signed.asc --export-key e431f0ce gpg --send-keys e431f0ce
That outputs the key to an ASCII file named signed.asc, which you can send as an attachment. It also attempts to post to the keyserver you listed in your ~/.gnupg/options file.
For further details on key signings see the GnuPG Keysigning Party HOWTO
Oh yeah, in the mutt documentation (part of the RPM) there's a recommendation to add the following to your ~/.procmailrc I don't know procmail, so I'm not certain if this is actually doing anything for or against me, but I gather it helps mutt cope with older style PGP messages.
##
## PGP
##
## As suggested by mutt documentation. (See PGP-Notes.txt.)
##
:0
* !^Content-Type: message/
* !^Content-Type: multipart/
* !^Content-Type: application/pgp
{
:0 fBw
* ^-----BEGIN PGP MESSAGE-----
* ^-----END PGP MESSAGE-----
| formail \
-i "Content-Type: application/pgp; format=text; x-action=encrypt"
:0 fBw
* ^-----BEGIN PGP SIGNED MESSAGE-----
* ^-----BEGIN PGP SIGNATURE-----
* ^-----END PGP SIGNATURE-----
| formail \
-i "Content-Type: application/pgp; format=text; x-action=sign"
}
Apparently that's the old way to do things. The manual also says "The new way is to leave headers alone and use mutt's check-traditional-pgp function, which can detect PGP messages at run-time, and adjust content-types."
That about covers what I've done with keys, signatures, encryption, etc.
ACKNOWLEDGEMENTS
I'd like to thank Dr. Garrison Q. Kenny (mentioned below), and Federico Grau for his help in getting me going with all this stuff.
REFERENCES (some of which I've actually looked at)